4 - Hash and VDF chains
A key ingredient in longest-chain blockchains are hash-chains as discussed in §4.1 below. While also uses a hash-chain (for the foliage chain ), for we use a new chaining structure called a VDF chain defined in §4.2 below.
4.1 Hash chains
For this writeup, a hash chain is a sequence of blocks, where each block contains some data value (possibly empty) and (with the exception of ) a hash value of the current data and the previous block.
Security from hash chains.
A hash chain is immutable in the following sense:
Proposition 2 (immutability of hash chains). If is a collision-resistant hash function, then it is computationally infeasible to find two distinct hash chains and where and no chain is a prefix of the other (which holds if they start with the same ).
4.2 VDF chains
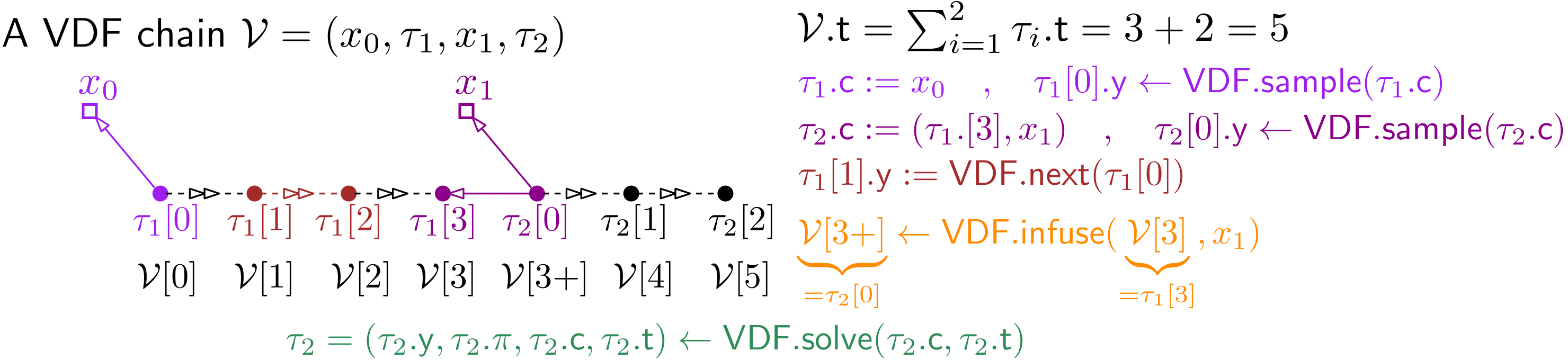
A VDF chain is a sequence
alternating data values and VDF values (as described in §A.3). The chain is valid if all VDF proofs are correct
and the challenge for the th VDF is derived from the previous VDF output (except for ) and data value
where we use the convention that is the empty string.
4.2.1 Notation for VDF chains
We naturally extend the notion for VDFs as described in §A.3 to VDF chains. The total number of VDF steps in a VDF chain as in eq.(5) is simply the sum of the steps in its VDFs
Security from VDF chains.
VDF chains give two basic security guarantees, the first is immutability analogous to hash chains, but also sequentiality inherited from the underlying VDF, we discuss them shortly in more detail.
Proposition 3 (immutability and sequentiality of VDF chains). Like a hash chain, a VDF chain is immutable in the sense that it's computationally infeasible to come up with two different VDF chains
where the last VDF outputs collide, i.e., . Here different means that either they have different length and neither is a prefix of the other. Or (if ) there exists an s.t. either or or . Note that we ignore the proofs when comparing chains (we just use them to determine whether the chain is valid) as they must not be unique.
Moreover a VDF chain is sequential, meaning that not only the individual VDFs must be computed sequentially (which follows from the security definition of VDFs), but also the VDFs in the chain were computed sequentially. I.e., computing a chain as above requires sequential steps.